AI Agents and Agentic AI – The time is now!

There is a paradig-level transition from generative interfaces to autonomous agentic ecosystems. We are witnessing the maturation of AI from advisory text-generators to operational entities capable of high-fidelity tool use and cross-platform execution. The convergence of standardized connectivity protocols like MCP, robust orchestration frameworks, and enterprise-grade governance marks the end of the “experimentation era.” As agents move from sandboxed demos to production environments, the focus shifts toward determinism, observability, and security. This evolution redefines the enterprise stack, positioning agents not as peripheral tools, but as the central fabric of modern digital labour and strategic automation.
Here are 25 real-world developments:
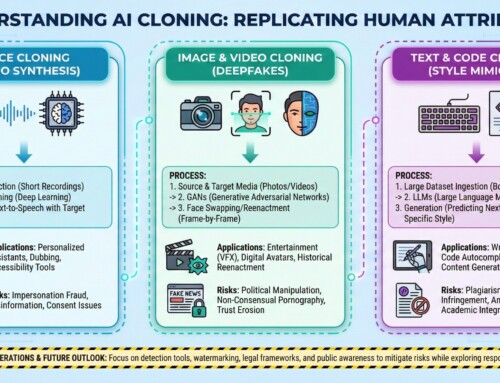
1. Agents shifted from “chat” to “do” via tool use
This change made agents operational rather than advisory, enabling them to trigger APIs, databases, workflows, and external systems instead of just responding with text. It marked the transition from conversational assistants to task-executing software components. As a result, agents could be embedded directly into business processes such as ticket resolution, data updates, and system monitoring.
2. OpenAI’s Agents SDK became a production path
The SDK signaled a move away from toy demos toward structured orchestration, memory handling, and controlled tool execution suitable for real applications. It provided developers with standardized patterns for managing agent state, retries, and failure handling. This lowered the barrier for enterprises to deploy agents reliably at scale.
3. Computer-using agents went mainstream
By enabling agents to click, type, scroll, and navigate interfaces, automation expanded beyond API-ready systems into legacy and consumer software. This allowed AI agents to operate in environments where no programmatic integration existed. However, it also exposed new risks related to brittleness, UI changes, and unintended actions.
4. Anthropic introduced “computer use” for Claude
This capability demonstrated that GUI-level control is viable but fragile, requiring heavy safeguards to avoid unintended actions. It highlighted the importance of permission boundaries, sandboxing, and human oversight. The release reinforced that visual agents are powerful but unsuitable for fully autonomous deployment in high-risk settings.
5. A real standard emerged for agent connectivity: MCP
MCP reduced fragmentation by defining a consistent way for agents to access tools, files, and services without custom integrations. This enabled interoperability across models, vendors, and execution environments. Standardization also made it easier to audit, secure, and govern agent behaviour. An excellent collection of learning videos awaits you on our Youtube channel.
6. MCP governance moved to a Linux Foundation-backed effort
Placing MCP under neutral governance increased trust among vendors and accelerated adoption across competing ecosystems. It reduced concerns about single-vendor control over a foundational agent protocol. Foundation-backed stewardship also enabled clearer contribution rules, long-term maintenance, and transparent evolution.
7. Google added official MCP support for Google services
This move validated MCP as an enterprise-grade protocol rather than a vendor-specific experiment. It signaled that large cloud providers were willing to align on shared agent infrastructure standards. Integration with Google services also made MCP immediately usable in production environments.
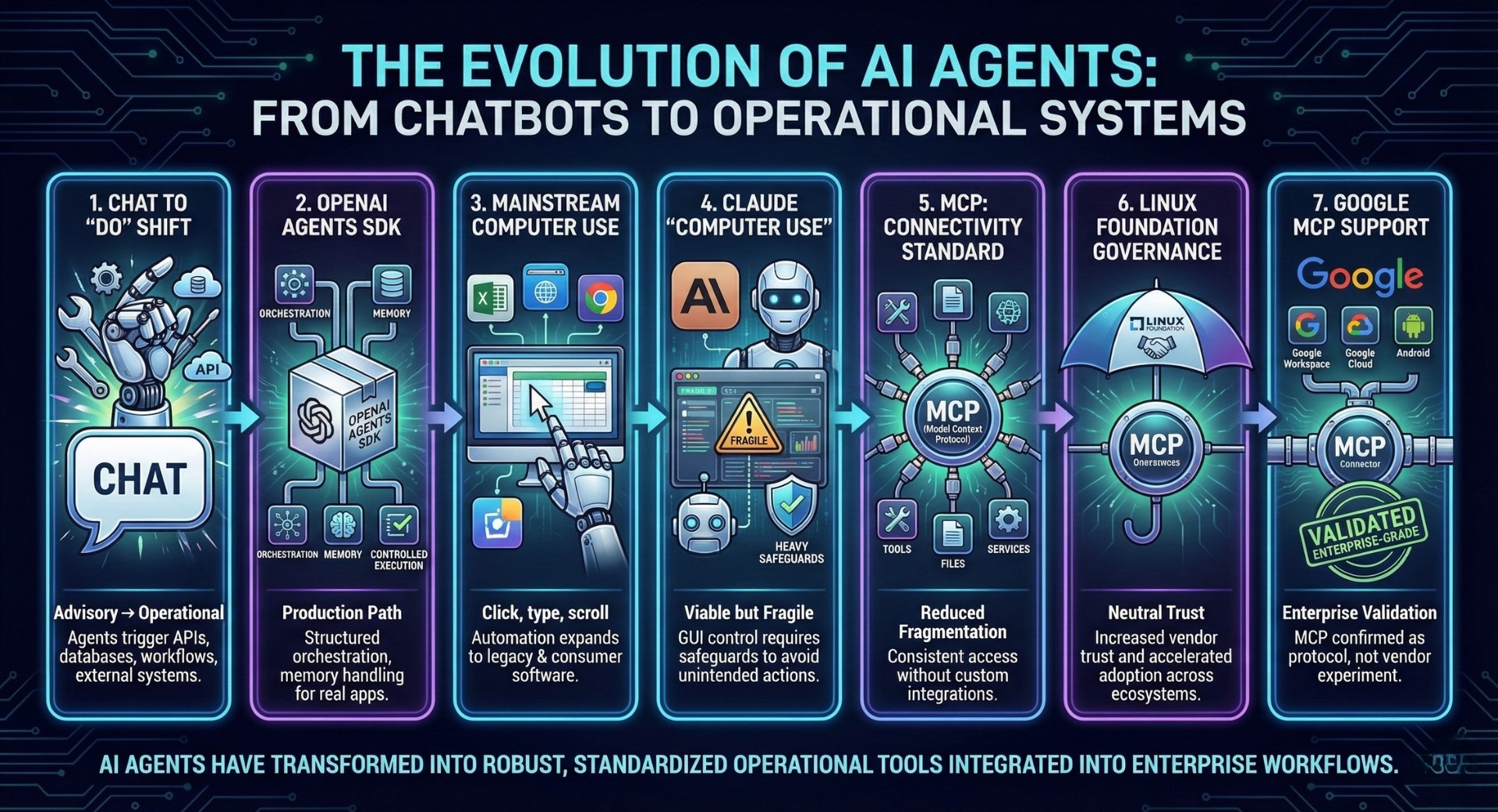
8. Enterprise agent platforms solidified with Vertex AI Agent Builder
Google positioned agents as first-class cloud resources, complete with deployment, monitoring, and access controls. This shifted agents from experimental workflows into managed infrastructure components. Enterprises gained clearer visibility into agent behavior, cost, and performance.
9. Google formalized agent-to-agent and payments concepts
These protocols hinted at future ecosystems where agents negotiate, transact, and coordinate autonomously under policy constraints. They introduced early design patterns for identity, authorization, and economic interaction between agents. The emphasis remained on controlled autonomy rather than unrestricted self-directed behavior.
10. AWS made Agents for Amazon Bedrock mainstream
Bedrock agents emphasized reliability, determinism, and security over novelty, aligning with enterprise risk expectations. AWS integrated agents tightly with existing IAM, logging, and compliance tooling. This made agent deployment feasible in regulated and mission-critical environments. A constantly updated Whatsapp channel awaits your participation.
11. Salesforce pushed the “agentic enterprise” with Agentforce
Agentforce reframed CRM workflows as agent-driven processes rather than static automation rules. It positioned agents as active participants that reason across customer data, tasks, and business objectives. This marked a shift from rule-based CRM automation to goal-oriented execution.
12. Agent observability became a product category
The industry recognized that unobservable agents create operational and legal risk at scale. New tools emerged to track agent decisions, tool calls, memory usage, and outcomes. Observability became essential for debugging failures, enforcing policy, and meeting compliance requirements.
13. ServiceNow positioned itself as an AI agent control tower
This approach treated agents as digital employees requiring governance, auditability, and lifecycle management. ServiceNow emphasized role definitions, approval flows, and performance tracking for agents. The framing aligned agent deployment with enterprise IT service management practices.
14. Security research exposed second-order prompt injection risks
These findings showed that multi-agent systems can amplify vulnerabilities through trust relationships between agents. An agent compromised via indirect input could influence downstream agents without direct user interaction. This shifted security focus from single prompts to multi-step agent interactions.
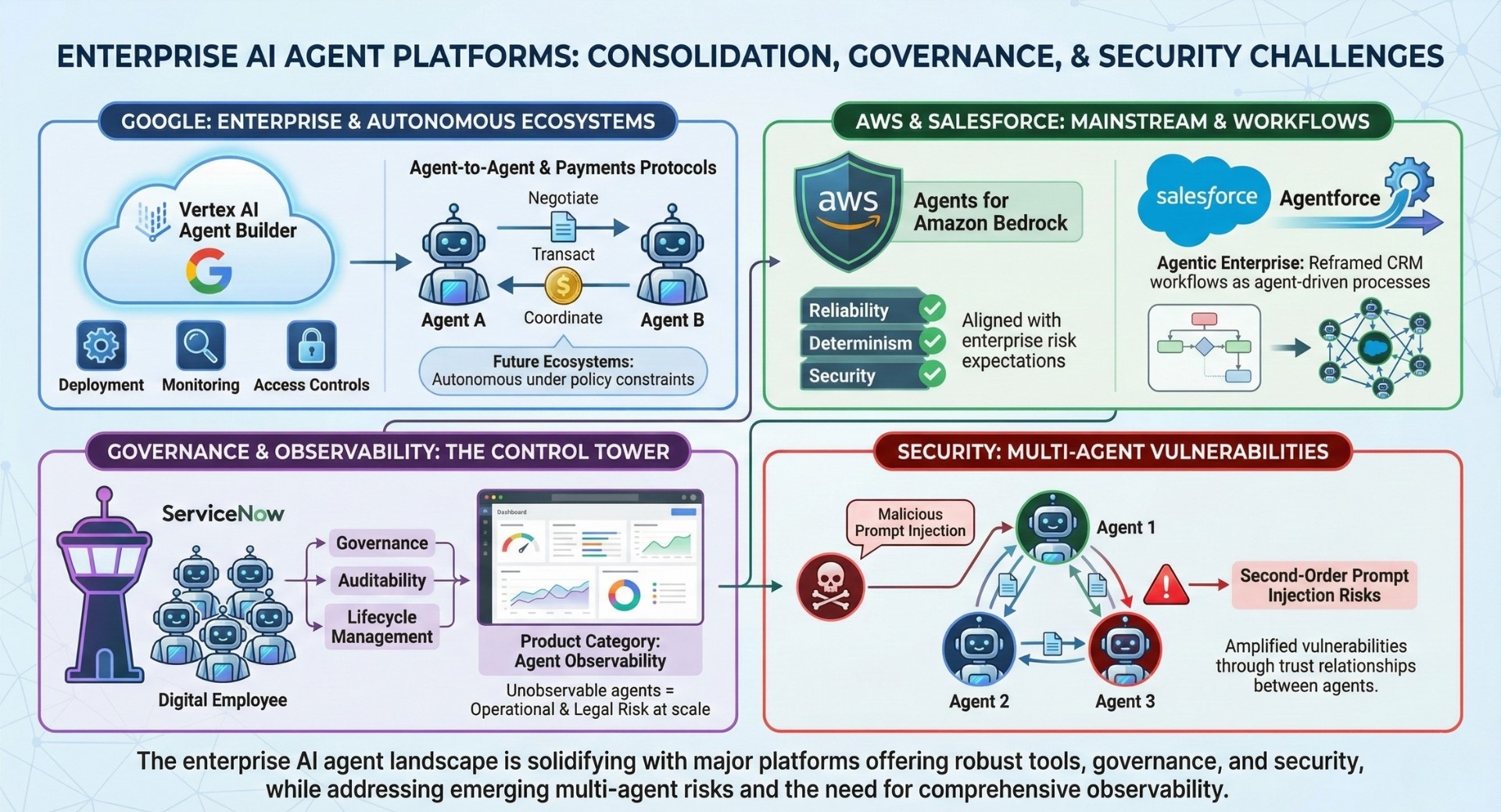
15. OWASP formalized agent-era security priorities
The guidance made clear that agentic systems require new threat models beyond traditional application security. It highlighted risks such as excessive autonomy, unsafe tool use, and cross-agent data leakage. This formalization helped security teams adapt controls for agent-based architectures. Excellent individualised mentoring programmes available.
16. Microsoft Copilot Studio matured into an agent-building hub
Copilot Studio lowered the barrier for enterprises to deploy agents within familiar Microsoft environments. It integrated agent creation with tools such as Microsoft 365, Power Platform, and Azure services. This allowed organizations to embed agents directly into existing productivity and business workflows.
17. Microsoft rolled out computer-use-style capabilities for agents
This bridged gaps where APIs do not exist, but also increased the need for human oversight. Agents could interact with legacy systems and graphical interfaces previously inaccessible to automation. The approach required stronger guardrails to prevent unintended actions and cascading errors.
18. LangGraph and LangChain reached v1.0
Stability signaled that agent orchestration patterns were maturing beyond rapid experimentation. Versioned releases provided clearer guarantees around APIs and behavior. This enabled teams to build longer-lived agent systems without constant refactoring.
19. AutoGen became foundational for multi-agent research and practice
It helped standardize how agents collaborate, debate, and divide tasks programmatically. AutoGen enabled structured interaction patterns such as role specialization and message passing. These patterns influenced both academic research and applied enterprise systems.
20. No-code and low-code agent building gained credibility
These tools expanded agent creation beyond engineers, while raising new governance challenges. Business users could assemble agents using visual workflows and prebuilt components. This increased the risk of shadow agents operating without formal oversight. Subscribe to our free AI newsletter now.
21. Agent evaluation matured with SWE-bench Verified
The benchmark grounded agent claims in measurable performance on real software tasks. It focused on end-to-end task completion rather than synthetic reasoning tests. This helped separate marketing claims from demonstrable capability.
22. Live evaluation emerged to reduce benchmark gaming
Rolling benchmarks acknowledged that static tests quickly become obsolete in fast-moving AI systems. Continuous evaluation reduced incentives to overfit to fixed test sets. This approach better reflected real-world deployment conditions.
23. Commercial “AI software engineer” agents entered the market
These products demonstrated impressive task completion but struggled with reliability, cost, and supervision. Human engineers were still required to review outputs and correct failures. Early deployments highlighted limits to full autonomy in complex engineering tasks.
24. Agentic automation blended agents with RPA
This fusion allowed dynamic decision-making on top of deterministic automation pipelines. Agents handled judgment and exceptions while RPA executed repeatable steps. The combination improved flexibility without abandoning control.
25. Consumer agent failures clarified real-world limits
High-profile failures showed that autonomy without robustness erodes trust faster than it builds excitement. Users reacted strongly to errors that caused financial or reputational harm. These incidents reinforced the need for staged deployment and clear accountability. Upgrade your AI-readiness with our masterclass.
Summary:
The Agentic AI landscape has now solidified around interoperability and governance, anchored by the Linux Foundation-backed Model Context Protocol (MCP). Industry leaders – OpenAI, Anthropic, Google, and Microsoft – have pivoted toward computer-use capabilities and structured SDKs, bridging the gap between modern APIs and legacy interfaces. Meanwhile, Salesforce and ServiceNow are competing to provide the orchestration layer for the “agentic enterprise.”
This expansion introduces complex risks, notably second-order prompt injection and operational fragility. Ultimately, the industry is moving toward a standardized agentic infrastructure where success is measured by reliability, measurable performance via benchmarks like SWE-bench, and rigorous security frameworks.